Cryptocurrency users face an ever-growing threat from phishing scams designed to compromise their security. Among the most targeted are users of Ledger, a leading manufacturer of hardware wallets for securing digital assets. To help protect yourself and your funds, it’s essential to know answers to the two questions: “What are Ledgers legit emails?” and “How to recognize phishing attempts.”

Additionally, this article examines the Ledger Recovery Phrase Verification email scam, explaining how it operates and offering tips to safeguard your assets from similar threats.
The Ledger Recovery Phrase Verification Email Scam
Before discussing “What are Ledgers legit emails?” you need to understand the common tricks scammers use. One of the most dangerous scams targeting cryptocurrency users is the Ledger Recovery Phrase Verification email scam. This sophisticated phishing attack deceives victims into sharing their recovery phrases, giving scammers complete access to their wallets and funds.
How It Works
- Phishing Email Creation
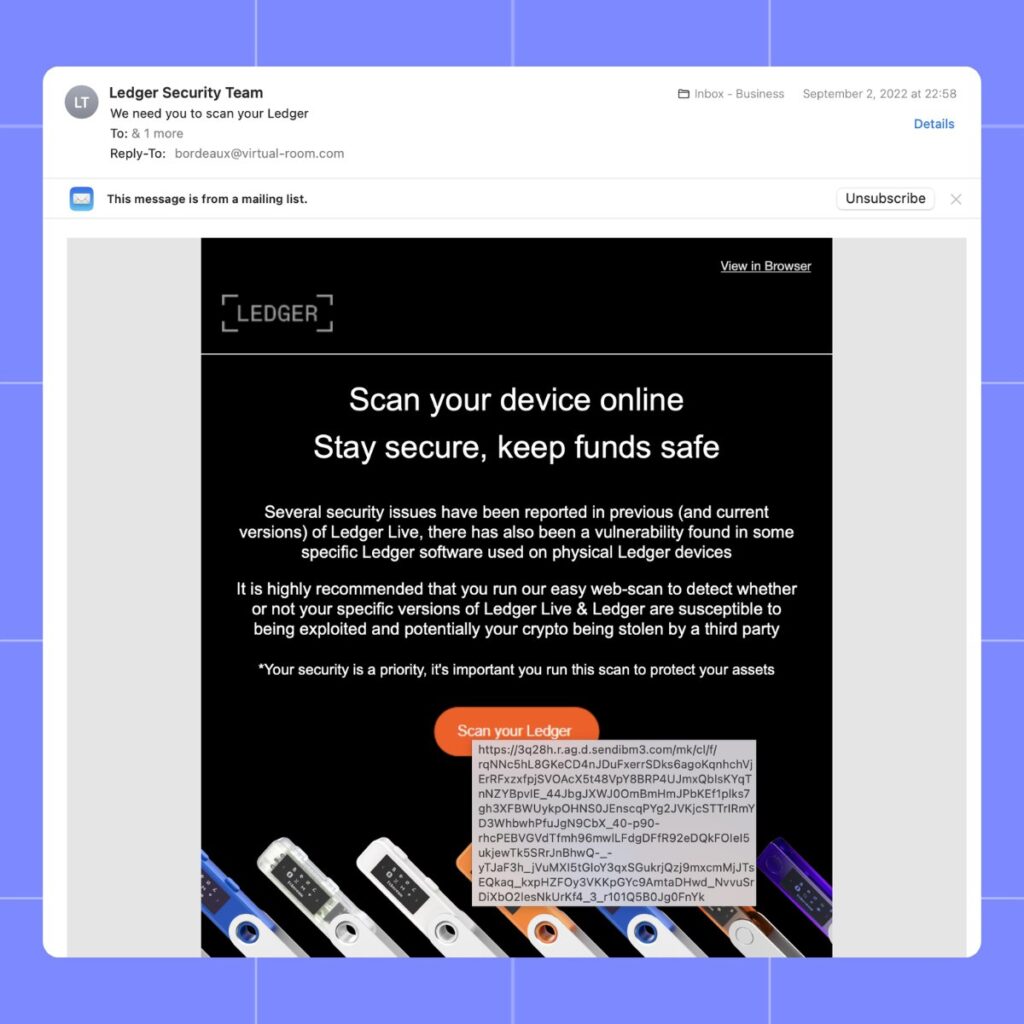
Scammers craft emails that mimic official Ledger communications. These emails often use Ledger branding, logos, and professional templates to appear legitimate. The subject line typically conveys urgency, such as “Action Required: Ledger Data Breach—Verify Your Recovery Phrase.” - Claiming a Data Breach
The email alleges a recent data breach affecting Ledger’s service, emphasizing that recovery phrases might have been exposed. It then urges users to verify their recovery phrase to “ensure their assets remain secure.” - Directing Users to a Fake Website
A link in the email redirects users to a phishing site designed to look like Ledger’s official platform. These websites often use similar URLs to Ledger, such as “ledger-access.com,” to trick users. - Requesting Recovery Phrase Input
The phishing site presents a form for users to input their recovery phrases, falsely claiming that this will help verify their wallet’s security. - Stealing and Exploiting Recovery Phrases
Once a user submits their recovery phrase, scammers gain full access to their cryptocurrency wallets, stealing all funds stored within.
Protecting Yourself from Phishing Scams
Knowing what are Ledger’s legit emails is your first step to security, but there’s more you can do to protect your assets:
- Verify Sender Information
- Double-check that emails come from one of Ledger’s verified addresses. Be cautious of addresses with subtle typos like “ledqer” or “legder.”
- Use tools like ConvertCase to analyze suspicious capitalization.
- Examine Links Carefully
- Hover over links to verify their destination. Genuine links should lead to Ledger’s official domains.
- Keep Recovery Phrases Private
- Ledger will never ask for your recovery phrase via email, phone, or any online platform.
- Store your recovery phrase offline and never share it with anyone.
- Report Suspicious Emails and Calls
- If you receive a phishing email, save it as a .EML or .HTML file and send it to [email protected].
- Ledger does not contact users via phone. If you receive a suspicious call, hang up and report the phone number.
What Are Ledgers Legit Emails?
To be sure you can identify genuine Ledger communications from fake ones, please be aware of the company’s authenticated email addresses. Below is the total number of all official email addresses Ledger uses:
- Marketing Emails
- Sender Name: Katie or Milan from Ledger
- Email Address: [email protected]
- Reply Address: [email protected]
- Transactional Emails
- Sender Name: Ledger
- Email Address: [email protected]
- Reply Address: [email protected]
- Support Emails
- Sender Name: Ledger Support
- Email Address: [email protected]
- Reply Address: [email protected]
- Delivery Notifications
- Sender Name: Ledger
- Email Address: [email protected]
- Reply Address: [email protected]
Important Notes:
Emails from Ledger may include links beginning with “go.ledger.” These links are safe as long as the email originates from a verified Ledger address.
If you require support via email, you will receive replies under the @ledger.fr or @ledger.com domain. These emails are from Legder’s support team.
Steps to Take If You’ve Been Scammed
If you suspect you’ve fallen victim to a phishing scam:
- Act Immediately
Transfer your funds to a new wallet secured with a fresh recovery phrase. - Report the Incident
Notify Ledger and your local authorities about the phishing attempt. - Enhance Your Security
Enable two-factor authentication (2FA) on your accounts and check email settings for unauthorized access.
Frequently Asked Questions
What Is a Recovery Phrase?
A recovery phrase, or seed phrase, is a series of words that acts as a backup to access and restore cryptocurrency wallets. If compromised, it can grant full access to your funds. We have mentioned this several times in our Ethereum Wallets article.
How Can I Identify a Legitimate Ledger Email?
Verify the sender’s email address against Ledger’s official list. Be wary of slight variations in spelling or suspicious links.
What If I Suspect a Phishing Email?
Do not click on links or provide any information. Report the email to [email protected] for further investigation.
Conclusion
Such scams, like Ledger Recovery Phrase Verification mail, set crypto owners exposed to so many threats. Of course, knowing which emails are actually coming from Ledger will protect your fortune. Companies, like Ledger, would never request the recovery phrase via email, phone call, or online form.
Be very cautious about unsolicited letters. Check senders’ addresses, avoid suspicious links, and report phishing emails at once. Informed and observant—that is how you will protect your assets with confidence in the digital space.
Stay vigilant, and remember: Your recovery phrase is the key to your wallet. Protect it at all costs.
Share on Social Media:
